Strengthen your Security with Professional PenTesting
In today’s evolving threat landscape, ensuring your IT systems are secure is more critical than ever. Our Penetration Testing service, delivered in collaboration with a trusted third-party provider, offers a comprehensive solution to test and improve the security of your organization’s networks, applications, and infrastructure.
What is Penetration Testing?
Penetration Testing (PenTesting) is a controlled, ethical hacking process that simulates a cyberattack against your systems to identify vulnerabilities and assess your security posture. Our certified security experts attempt to exploit potential weaknesses in your defenses, providing you with a detailed report on any vulnerabilities and actionable recommendations to fortify your systems.
Why Choose our PenTesting Service?
- Comprehensive Coverage: We test across networks, applications, cloud environments, and more, ensuring no weak spots are left unexamined.
- Real-World Attack Simulation: Our approach simulates real-world attacks from malicious hackers, giving you insight into how your systems would hold up against genuine threats.
- Detailed Reporting: You will receive a thorough, easy-to-understand report that outlines the vulnerabilities found, the level of risk they present, and recommended steps for remediation.
- Proactive Security: Identifying and fixing vulnerabilities before they can be exploited is essential to avoiding costly data breaches and downtime.
- Industry Expertise: As a trusted partner of various certified experts, we bring advanced tools and methodologies to ensure your security is aligned with best practices.

Test Your Defenses
See what a hacker sees on your network before they do.
AS-PenTest is essentially a hacker on a company’s network. It looks for sensitive data, performs exploits, conducts man-in-the-middle attacks, crack password hashes, escalates privileges on the network, and even impersonates users to find sensitive data. It goes beyond identifying vulnerabilities by actually exploiting them to demonstrate what happens if an attacker got access to the network.
Key Features of Our PenTesting Service:
- Network and application security testing
- Simulated attacks on web applications and cloud infrastructure
- Vulnerability analysis and risk prioritization
- Custom remediation recommendations
- Post-test consultation and guidance
Who Can Benefit from PenTesting?
- Small to Medium-Sized Businesses (SMBs): Secure your infrastructure and protect customer data from malicious attacks.
- Enterprises: Test complex systems and applications, ensuring that your multi-layered security is effective.
- Regulated Industries: Meet compliance requirements by regularly testing your security defenses and safeguarding sensitive information.
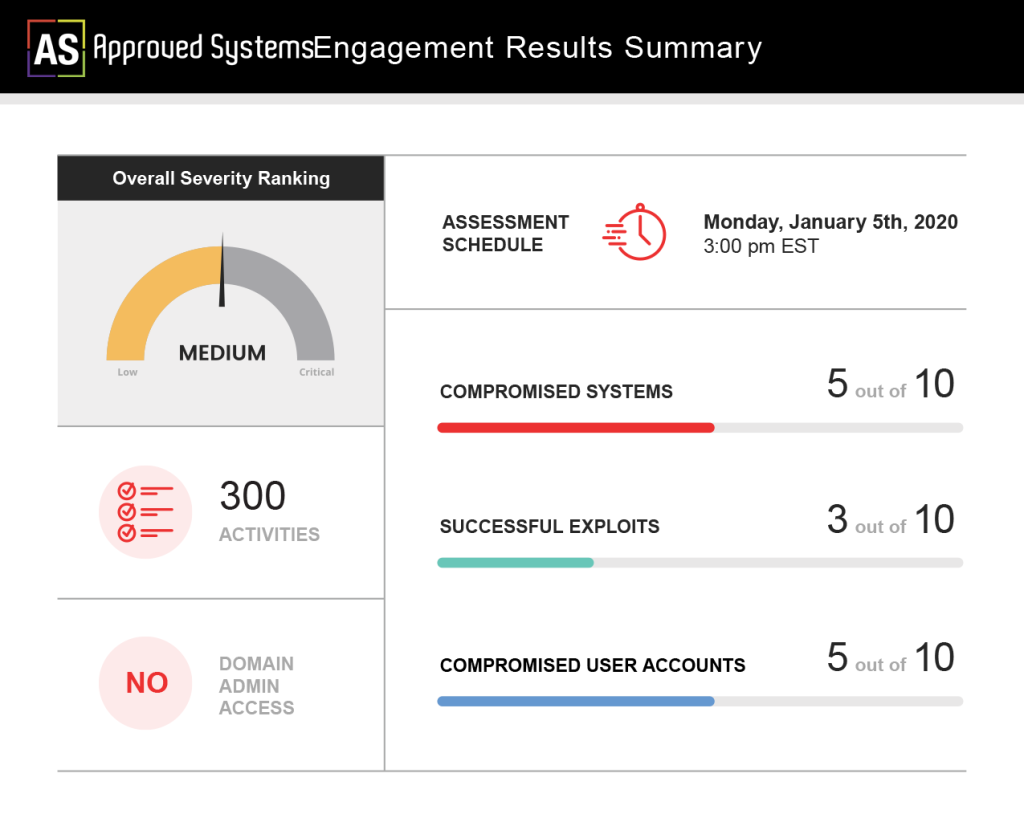
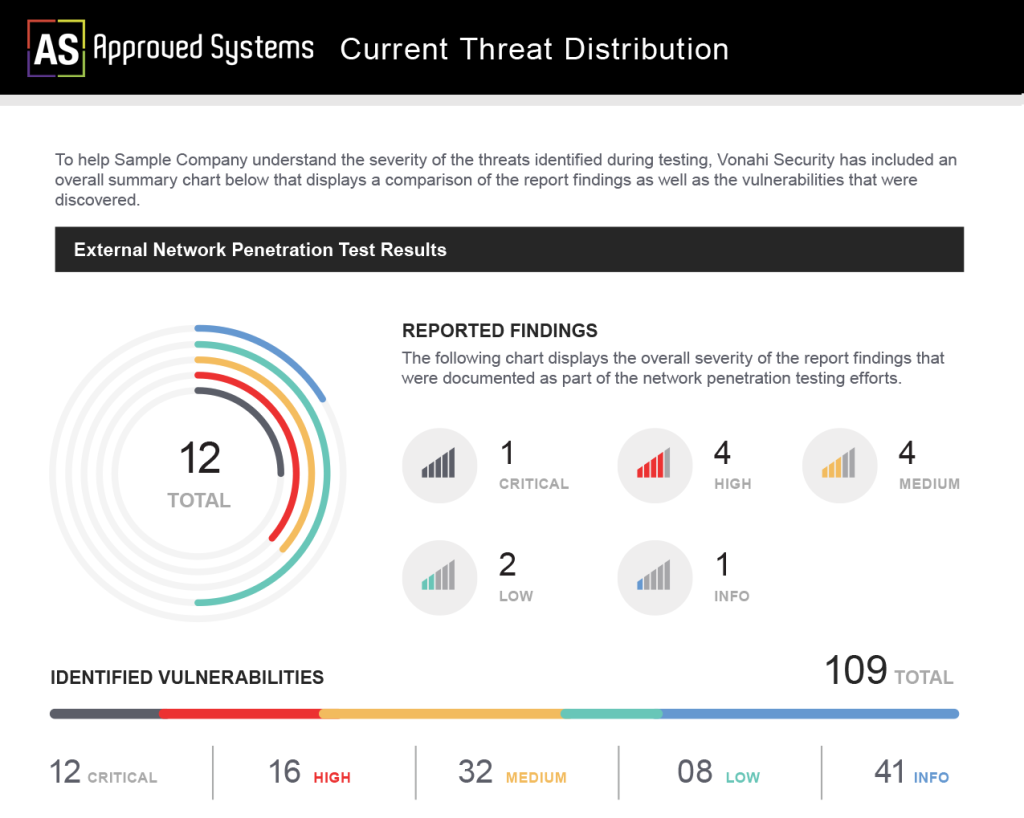
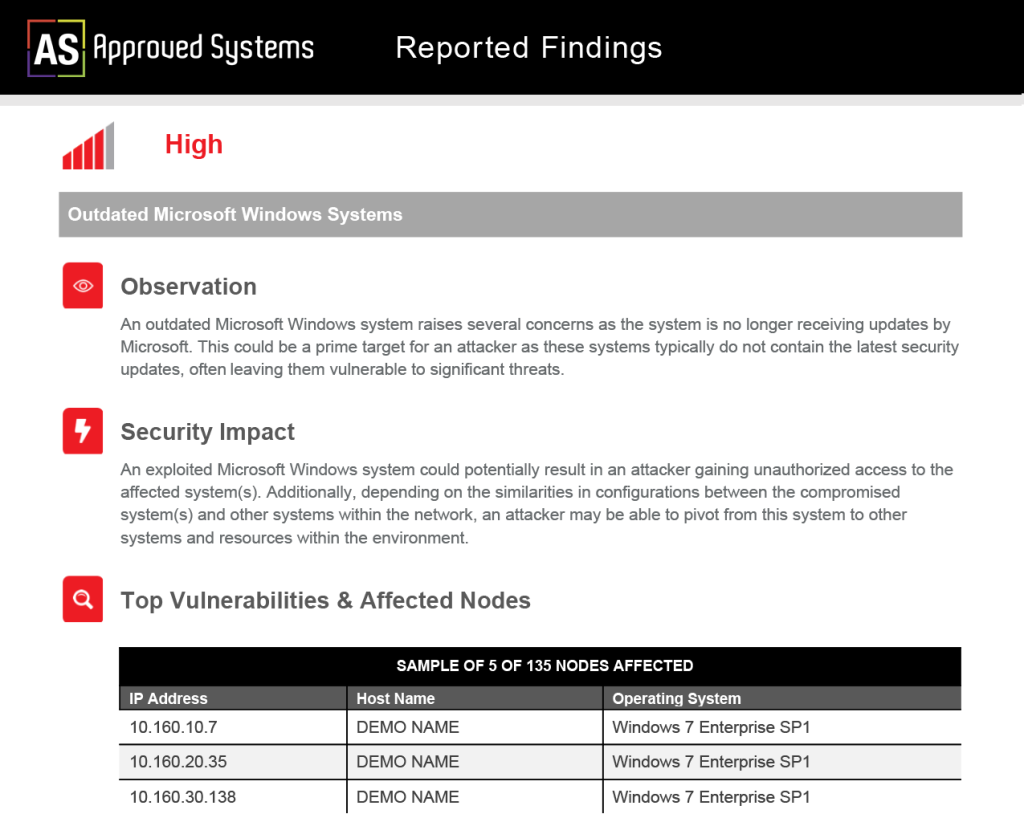
Quality Reports to Share with the Team
External vs. Internal Pen Testing
Our PenTesting service includes both External and Internal testing options, ensuring that every aspect of your infrastructure is thoroughly examined for potential vulnerabilities.
| External Penetration Testing | Internal Penetration Testing |
|---|---|
| Focus: External PenTesting simulates an attack originating from outside your organization. This test is essential for identifying vulnerabilities in your perimeter defenses, including firewalls, web applications, and exposed services. | Focus: Internal PenTesting simulates an attack from within your network, often mimicking insider threats or compromised employee accounts. This test is crucial for identifying weaknesses in access control, internal network segmentation, and privilege escalation. |
| Purpose: This type of testing helps assess how well your network and applications can withstand an attack from outside, including hackers attempting to breach your systems remotely. It covers vulnerabilities in internet-facing applications and services. | Purpose: Internal testing focuses on the damage a malicious actor with internal access (e.g., a disgruntled employee or compromised account) could do. It tests the security of sensitive internal systems, database access, and internal communications. |
| Best For: Companies concerned about internet-facing services, web applications, and external attacks. | Best For: Organizations looking to strengthen their internal security posture, ensuring that critical data remains safe from insider threats. |
| Typical Scenarios: Testing firewalls, VPNs, web applications, and public-facing services. | Typical Scenarios: Testing internal networks, employee access controls, and lateral movement within systems. |
Stay Compliant and Secure
Our PenTesting services help businesses stay compliant with industry standards such as CREST, ISO 27001, SOC 2, GDPR, and HIPAA.
Regular penetration testing helps ensure your data is safe and your business meets regulatory requirements.
Ready to Secure Your Organisation?
Protect your business from evolving cyber threats by booking a Penetration Test today. Our team is here to assist with any questions and provide more information about how our service can help you achieve a robust security posture.
Contact Us to learn more about our PenTesting services and schedule a consultation.
Complimentary Pentest
We are offering for a limited time a complmentary external exploratory PenTest for your Business.
What’s Included in the Test?
- Network Footprinting & Reconnaissance
- Identifies publicly accessible IP addresses and open ports.
- Discovers publicly known vulnerabilities associated with exposed services.
- Automated Vulnerability Scanning
- Uses industry-leading scanning tools to detect misconfigurations and security flaws.
- Highlights common issues such as outdated software, weak encryption, and misconfigured services.
- Risk Analysis & Prioritization
- Categorizes vulnerabilities based on severity (low, medium, high, critical).
- Provides an impact assessment to help prioritize remediation efforts.
- Report & Recommendations
- A detailed report outlining identified risks and recommended mitigations.
- Guidance on security best practices to harden your external-facing infrastructure.